So with all that’s going on a lot of people are having trouble keeping up with setting up VPNs correctly. I’ve also struggled with clients that do not have a cloud only solution but are still on a hybrid method of working.
In the past I’ve talked about Always On VPN which we tend to deploy at clients. This, and even just SSTP connections are our most used VPN method. I tend to like Microsoft solutions for everything. 😉 In any case – We’ve been having trouble with this too. Some people suggest using CMAK to assist in deploying VPN. Of course like using my RMM system instead. 😉
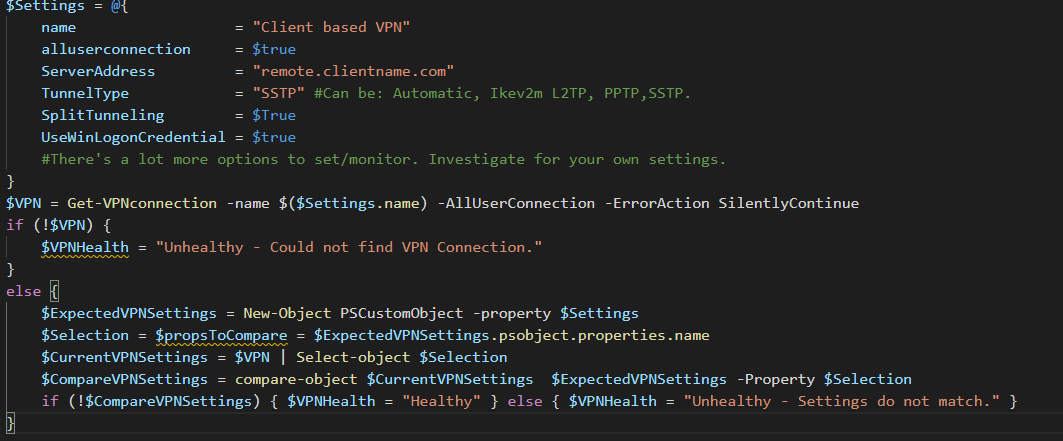
As with most of the blogs I’ve created two scripts; one for monitoring and one for remediation.
The monitoring script
In our RMM we can give each monitoring script a set of input variables. Using these input variables we check if the VPN is set the way we want it. If you can’t setup input variables on your RMM, just change them in the script.
|
|
So now that you are monitoring the VPN connection and if the settings are correct, we’re moving on to the remediation or setup side of the house.
Remediation script
the remediation works by looking up the current VPN connections based on the name property, if the VPN does not yet exists we will add one. If it does exists, we will reset the settings to the way we would like them to be.
|
|
What’s cool is that these scripts work for any VPN that uses the Windows VPN client. This makes it super simple to deploy and monitor your clients VPN connections, and always have the same settings across your entire customer base.
And that’s it! as always, Happy PowerShelling.