As an MSP we manage a lot of clients, and I’m pretty sure we’ve all been in situations where a client had some leavers in the company and not notify us as the administrators, or that the client had some very inactive users that don’t really need to be licensed or could be converted to a shared mailbox for example.
To help these clients we monitor the users activity and remove licenses when they are not required or start the off-boarding procedure when a client has someone has left the company. This often generates goodwill at our client and gives us the feeling of really being in control of each environment.
Another great side-effect of this monitoring script is being able to alert if users aren’t using all resources too; for example directly after a teams deployment you’ll want users to start showing Teams Activity. If they’re not, you can jump in on that and help with something like more user-training. So, lets get to scripting.
User Activity Report Monitoring
To use this script, you’ll need the Secure Application Model. You’ll also need some extra permissions on your application.
- Go to the Azure Portal.
- Click on Azure Active Directory, now click on “App Registrations”.
- Find your Secure App Model application. You can search based on the ApplicationID.
- Go to “API Permissions” and click Add a permission.
- Choose “Microsoft Graph” and “Application permission”.
- Search for “Reports” and click on “Reports.Read.All”. Click on add permission
- Do the same for “Delegate Permissions”.
- Finally, click on “Grant Admin Consent for Company Name.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
######### Secrets #########
$ApplicationId = 'YourApplicationID'
$ApplicationSecret = 'YourApplicationSecret' | ConvertTo-SecureString -Force -AsPlainText
$TenantID = 'YourTenantID'
$RefreshToken = 'VeryLongRefreshToken'
$UPN = "UPN-Used-to-Generate-Tokens"
$Skiplist = "bla1.onmicrosoft.com", "bla2.onmicrosoft.com"
######### Secrets #########
$AlertingDate = (get-date).AddMonths(-2) #two months of inactivity is our alerting moment.
#######
write-host "Generating token to log into Azure AD. Grabbing all tenants" -ForegroundColor Green
$credential = New-Object System.Management.Automation.PSCredential($ApplicationId, $ApplicationSecret)
$aadGraphToken = New-PartnerAccessToken -ApplicationId $ApplicationId -Credential $credential -RefreshToken $refreshToken -Scopes 'https://graph.windows.net/.default' -ServicePrincipal -Tenant $tenantID
$graphToken = New-PartnerAccessToken -ApplicationId $ApplicationId -Credential $credential -RefreshToken $refreshToken -Scopes 'https://graph.microsoft.com/.default' -ServicePrincipal -Tenant $tenantID
Connect-AzureAD -AadAccessToken $aadGraphToken.AccessToken -AccountId $upn -MsAccessToken $graphToken.AccessToken -TenantId $tenantID | Out-Null
$tenants = Get-AzureAdContract -All:$true
Disconnect-AzureAD
$ActivityReport = foreach ($Tenant in $Tenants | Where-Object {$\_.DefaultDomainName -notin $Skiplist}) {
write-host "Processing tenant $($tenant.displayname)"
$CustGraphToken = New-PartnerAccessToken -ApplicationId $ApplicationId -Credential $credential -RefreshToken $refreshToken -Scopes "https://graph.microsoft.com/.default" -ServicePrincipal -Tenant $tenant.CustomerContextId
$Header = @{
Authorization = "Bearer $($CustGraphToken.AccessToken)"
}
(Invoke-RestMethod -Uri "https://graph.microsoft.com/beta/reports/getOffice365ActiveUserDetail(period='D90')" -Headers $Header -Method get -ContentType "application/json") | ConvertFrom-Csv
}
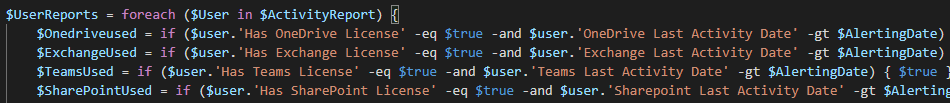
$UserReports = foreach ($User in $ActivityReport) {
$Onedriveused = if ($user.'Has OneDrive License' -eq $true -and $user.'OneDrive Last Activity Date' -gt $AlertingDate) { $true } else { $false }
$ExchangeUsed = if ($user.'Has Exchange License' -eq $true -and $user.'Exchange Last Activity Date' -gt $AlertingDate) { $true } else { $false }
$TeamsUsed = if ($user.'Has Teams License' -eq $true -and $user.'Teams Last Activity Date' -gt $AlertingDate) { $true } else { $false }
$SharePointUsed = if ($user.'Has SharePoint License' -eq $true -and $user.'Sharepoint Last Activity Date' -gt $AlertingDate) { $true } else { $false }
[PSCustomObject]@{
OneDriveUsed = $Onedriveused
ExchangeUsed = $ExchangeUsed
TeamsUsed = $TeamsUsed
SharePointUsed = $SharePointUsed
AssignedProduct = $user.'Assigned Products'
Username = $user.'User Principal Name'
Displayname = $user.'Display Name'
IsDeleted = $user.'Is Deleted'
DeletedOn = $user.'Deleted Date'
}
}
$UserReports | Out-GridView
|
This gives you a little grid to check out the data, you can also edit it easily to create a monitoring component out of it for your RMM.
And that’s it! As always, Happy PowerShelling