Microsoft has introduced web sign-in some months ago as an alternative way to log into Windows. Web Sign-in allows you to sign in using your M365 credentials and multifactor authentication token, or using a Azure AD Temporary Access Pass. Web-Sign in is pretty cool as users get presented with a modern authentication pop-up dialog when signing in, the same one they are used to seeing when logging into the Office suite applications.
One of the cool things you can bring with this is that you can enforce the user has to be online, and use MFA to log onto their windows device. Web sign-in is still a preview feature so don’t just go deploying it everywhere without considering the implications.
Enabling web sign-in can be done from Intune, or by using the small script below. I’ve also included an example to disable all other security providers so web sign-in becomes the only option to logon, of course you should use this at your own risk.
The Script
This script simply enables web sign-in. If you’d like to disable the password credentials provider you can uncomment the last line of the script.
1
2
3
4
5
6
7
8
|
if((Test-Path -LiteralPath "HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn") -ne $true) { New-Item "HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn" -force};
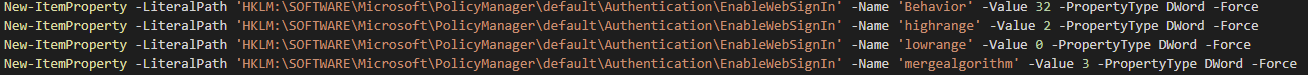
New-ItemProperty -LiteralPath 'HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn' -Name 'Behavior' -Value 32 -PropertyType DWord -Force
New-ItemProperty -LiteralPath 'HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn' -Name 'highrange' -Value 2 -PropertyType DWord -Force
New-ItemProperty -LiteralPath 'HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn' -Name 'lowrange' -Value 0 -PropertyType DWord -Force
New-ItemProperty -LiteralPath 'HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn' -Name 'mergealgorithm' -Value 3 -PropertyType DWord -Force
New-ItemProperty -LiteralPath 'HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn' -Name 'policytype' -Value 4 -PropertyType DWord -Force
New-ItemProperty -LiteralPath 'HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Authentication\EnableWebSignIn' -Name 'value' -Value 0 -PropertyType DWord -Force
#New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{60b78e88-ead8-445c-9cfd-0b87f74ea6cd}' -Name 'Disabled' -Value 1 -PropertyType DWORD -Force
|
This isn’t the only way to achieve multi-factor authentication on a Windows Device. There’s another cool blog post here about enabling MFA on windows devices, using a Bluetooth connection for example.
As always, Happy PowerShelling!