Hi All,
Today we will be focusing on monitoring the Compellent SAN status from a single server, Most Compellents are delivered with Dell’s Co-Pilot functionality and do not require you to monitor it yourself, but I also enjoy having an extra set of eyes on my shared storage – Also in some security restricted environments we cannot use the Co-pilot functionality and have to rely on our own monitoring sets.
Requirements:
- Compellent PowerShell components(Link)
- PowerShell v3 or higher
Creating the monitoring sets:
Creating the monitoring sets are very simple and straight-forward, after we install the Dell Compellent PowerShell Components we get the ability to connect to the SAN by importing the modules and using the Get-SCConnection cmdlet.
|
|
As you can see, this is not very secure – The password is stored plain-text in the script and could be read by anyone, so before moving on to the monitoring part we’re going to make sure we’re connecting more securely than just using plain-text credentials.
To start encrypting our credentials we’ll be generating a secure key to store as a file, this file will need to be placed in a secure location that no-one except you(or better: the script) can access it. I always advice that you create a new keypair for each script, so if for whatever reason one key is leaked to the public not all your scripts are affected.
|
|
After creating this key, we can start encrypting and decrypting passwords with it. To do this we’ll create a new password file.
|
|
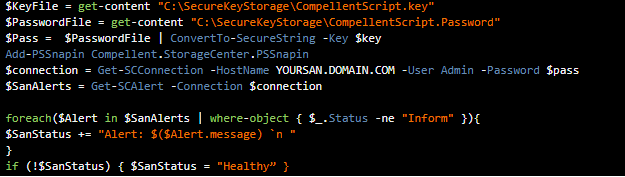
Now, we change our script to use the encrypted password+keyfile combination instead of the credentials object we’ve created before.
|
|
Now that we have connected to the SAN we can start retrieving the warning and errors using the following script:
|
|
And that’s it! You now have all Alerts from your SAN in one handy location, excluding the “INFORM” reports.